Why Data Breaches Start at Hiring, Not Hacking
 February 19th, 2026
February 19th, 2026
Most organisations think of background verification (BGV) as a hiring hygiene step. Important, yes, but often treated as a box to tick, not a business risk to manage.
That’s a dangerous misconception.
Because when background verification fails, or is skipped entirely, the consequences aren’t limited to a bad hire. They show up as data breaches, insider threats, compliance violations, and reputational damage that can take years (and crores) to recover from.
The Silent Risk Behind Data Breaches

According to a Data Breach Investigations Report by a major firm, insider threats driven by human behavior and error, including moonlighting, account for nearly 60% of global data breaches.
That’s not a technology failure.
That’s a people failure.
And it often starts with incomplete or ineffective background verification.
In India, the risk is growing fast:
- 73% of the workforce has considered or engaged in moonlighting for financial reasons.
- 43% of Indian IT employees believe moonlighting is acceptable, even when employment contracts say otherwise.
The estimated annual cost of productivity loss and data exposure linked to moonlighting exceeds ₹1,000 crores.
When individuals work multiple jobs, sometimes for competing organisations, without disclosure, the line between intentional misconduct and accidental data exposure blurs quickly.
How Weak Background Verification Enables Insider Threats
Most data breaches linked to insiders don’t involve malicious hackers. They involve:
- Employees with undisclosed dual employment
- Candidates who misrepresent past roles or employers
- Individuals with conflicts of interest that were never identified
- Access being granted to people who should never have had it
When background checks rely only on self-declared information, or skip employment and income verification entirely, organisations unknowingly grant access to:
- Source code
- Customer data
- Financial systems
- Internal IP
Once access is granted, damage can happen quietly and quickly.
Moonlighting: Not Just an Ethics Issue
Moonlighting isn’t merely a policy violation. It’s a data security risk.
Employees juggling multiple roles are:
- 40% more likely to show reduced productivity
- More prone to errors caused by divided focus
- Exposed to conflicts of interest, especially in similar or adjacent industries
Worse, employees working across companies may unintentionally reuse knowledge, tools, or data…creating legal and compliance exposure for both employers!
Consider this scenario:
An employee joins a mid-sized tech company in a developer role. During hiring, no employment or income verification is conducted, only resume checks and reference calls. What goes unnoticed is that the employee is already working full-time for another organization in a similar domain.
To manage both jobs, the employee:
- Uses the same personal laptop for both roles
- Switches between company VPNs and tools
- Reuses code snippets, frameworks, or documentation across projects to save time
Over time, sensitive information, from client logic to proprietary workflows to internal documentation, gets unintentionally shared across environments. There is no malicious intent. But the damage is done.
Now add one more layer:
The second employer happens to be a competitor or works with overlapping clients.
What began as undisclosed moonlighting snowballs into:
- A breach of confidentiality agreements
- An insider-led data exposure
- A legal and compliance nightmare for both organisations
And when investigated, the root cause isn’t hacking.
It’s a hiring blind spot.
This is why major organisations have taken firm action against moonlighting, including terminations. These cases aren’t about control. They’re about risk containment.
Why This Happens More Often Than Companies Think
Employees engaged in moonlighting often don’t see themselves as security risks. But divided attention, overlapping responsibilities, and pressure to perform increase the likelihood of data mishandling, credential misuse, and accidental sharing of sensitive information.
Compliance Just Can’t Be Optional Anymore
Employment contracts, data protection frameworks, and regulatory expectations are getting stricter. Undisclosed employment can violate:
- Confidentiality clauses
- Non-compete agreements
- Industry compliance requirements
- Client data protection obligations
When background verification is weak, organisations are left reacting to breaches instead of preventing them, often under regulatory scrutiny.
What Strong Background Verification Actually Does
Effective BGV isn’t about mistrust. It’s about risk intelligence.
Robust verification helps organisations:
- Validate employment history and income claims
- Detect dual employment and overlapping roles
- Identify shell companies or fabricated employers
- Reduce insider threat exposure before access is granted
- Protect sensitive data, systems, and IP
In other words, it shifts hiring from assumption to assurance.
How DigiVerifier Helps Reduce Data Breaches
DigiVerifier is built for exactly this challenge.
We help HR and compliance teams verify candidates quickly, securely, and responsibly using trusted government-backed data sources such as:
- EPFO
- ITR
- DigiLocker
- UAN records
Why we’re India’s #1 background verification establishment:
- Verifications happen in minutes, not weeks
- Explicit candidate consent is always obtained
- We use Government of India–approved systems
- Personal data is NOT stored, only verified
- Our solution is patented, licensed, and trusted across industries
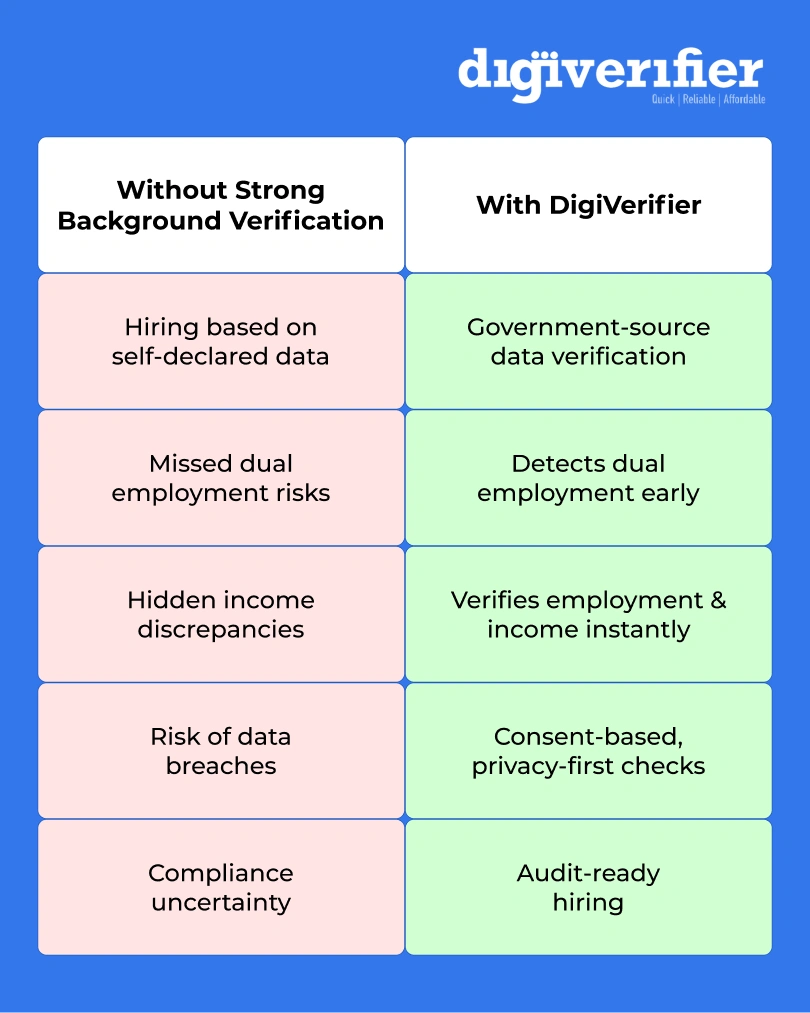
By identifying employment discrepancies, moonlighting risks, and false claims early, DigiVerifier helps organisations reduce exposure to insider threats before access is ever granted.
The Bottom Line
Data breaches don’t always start with hackers.
Sometimes, they start with a resume.
When background verification is weak, data security becomes fragile. And in today’s environment, that’s a risk no organisation can afford.
Strong hiring practices are no longer just about speed or cost.
They’re about trust, transparency, and protecting what matters most.
Because when you verify right, you don’t just hire better…you secure better!
